The hardware will probably survive a decade—but the software stack? That's where the real battles are fought.
We recently encountered a painful reality: a fleet of industrial PCs, hardware perfectly functional after 8 years of continuous operation, required complete replacement because their Windows Embedded Standard 7 installation had reached end-of-life. The security vulnerabilities made them unacceptable for network connectivity, and updating wasn't economically feasible. This scenario repeats constantly across the embedded landscape.
The Hardware-Software Mismatch
Modern embedded hardware has achieved remarkable longevity:
Industrial motherboards: 7-10 year production lifecycle
AMD embedded processors: 5+ year availability
Server components: 3-5 year refresh cycles
Meanwhile, software support timelines tell a different story:
Standard Linux LTS: 2-6 years
Windows IoT: 5-10 years (with expensive extended support)
Android: 3-5 years for most OEM distributions
Custom RTOS: Vendor-dependent, often 3-7 years
This mismatch creates a dangerous gap where functional hardware becomes obsolete due to software limitations.
The Four Horsemen of Software Obsolescence
1. Security Update Abandonment
The most immediate threat comes from unpatched vulnerabilities. Our analysis of embedded systems in industrial settings shows:
60% run operating systems no longer receiving security updates
35% have critical vulnerabilities with available patches that cannot be applied due to compatibility concerns
Only 5% maintain full security update compliance beyond 5 years
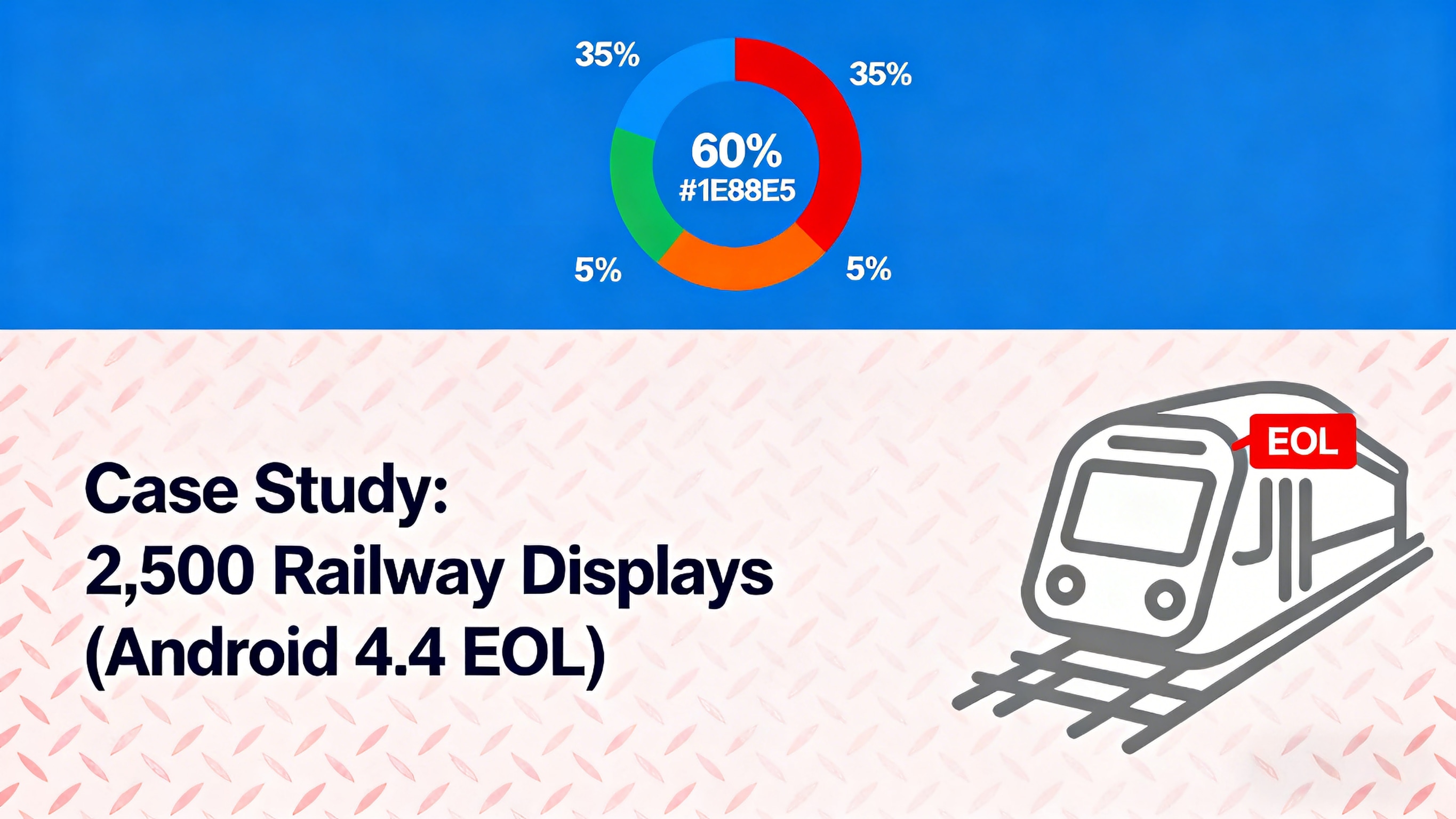
Case Study: The Railway Display Crisis
A European rail operator faced replacing 2,500 information displays because the original Android 4.4-based software stack:
Couldn't be updated to meet new security requirements
Lacked driver support for modern networking hardware
Contained proprietary middleware incompatible with newer Android versions
The hardware remained perfectly functional, but the software stack had reached a dead end.
2. Dependency Chain Collapse
Modern embedded systems rely on complex software dependency chains that inevitably break:
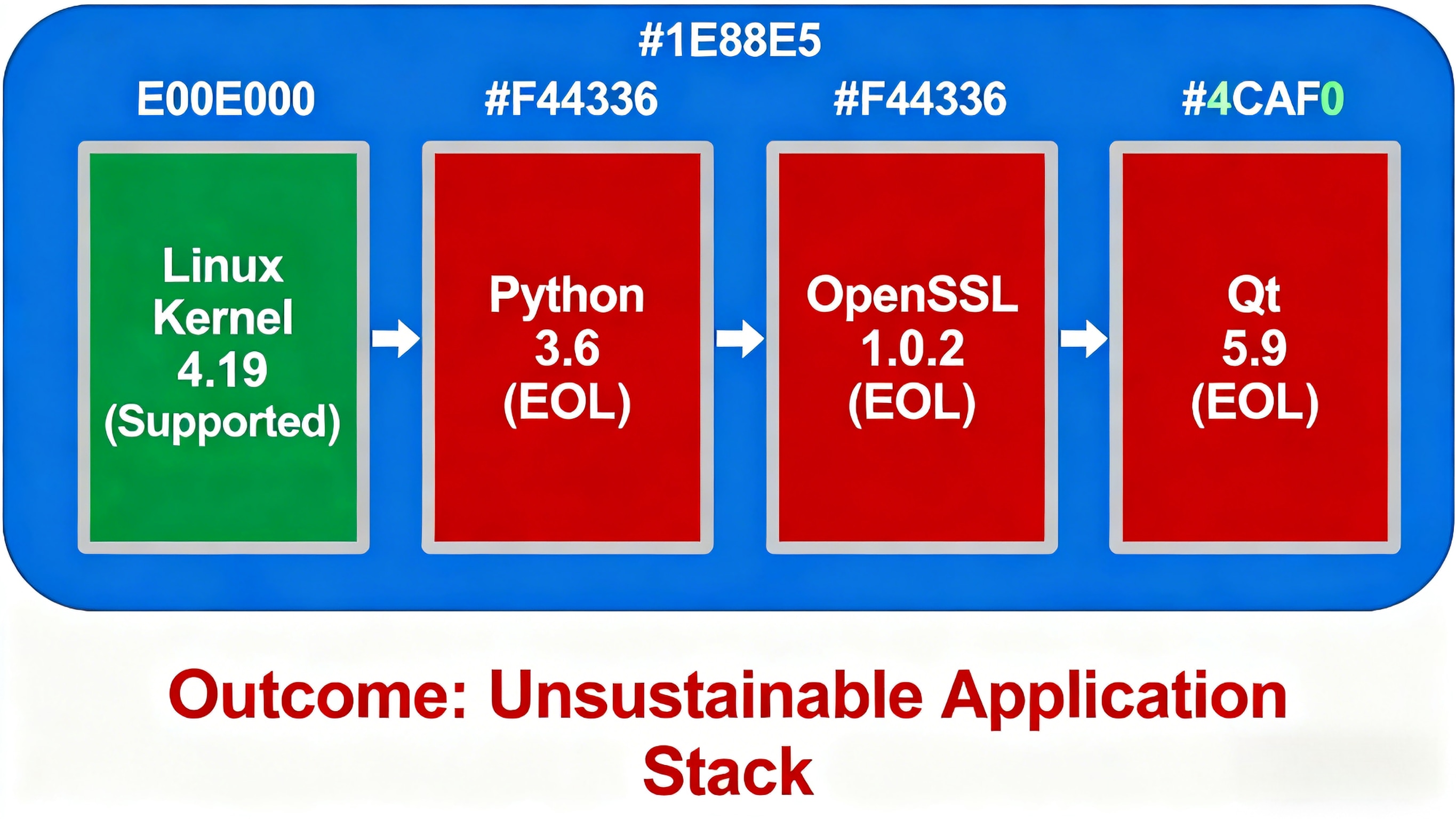
Real Example from Our Medical Device Practice:
A patient monitoring system built on:
Linux kernel 4.19 (supported)
Python 3.6 (EOL)
OpenSSL 1.0.2 (EOL)
Qt 5.9 (EOL)
Despite the kernel receiving updates, the application stack became unsustainable due to deprecated dependencies.
3. API and Framework Rot
As platforms evolve, APIs get deprecated and frameworks lose support:
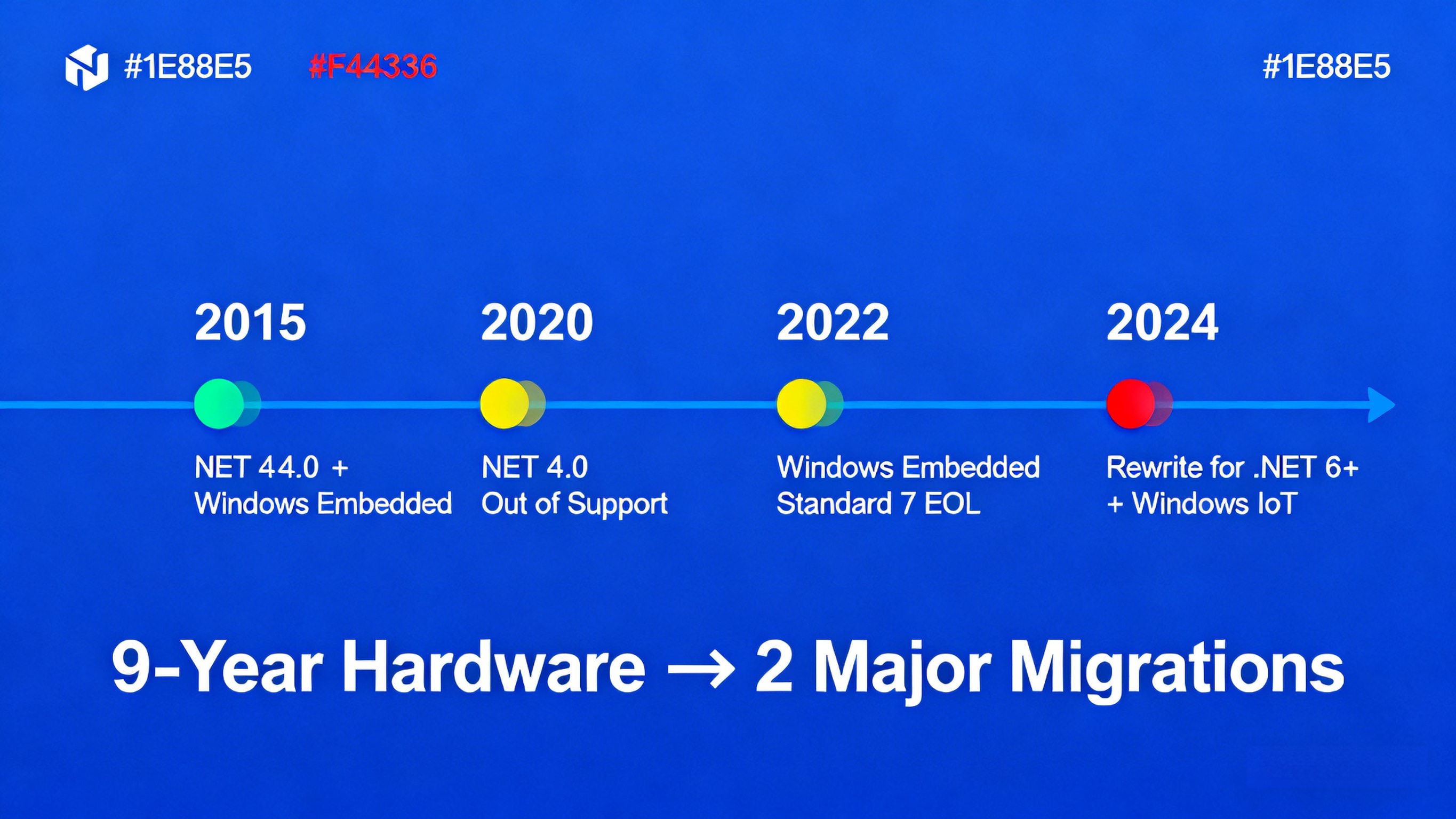
Industrial HMI Platform Migration
2015: Built on .NET Framework 4.0 with Windows Embedded
2020: .NET Framework 4.0 out of support
2022: Windows Embedded Standard 7 end-of-life
2024: Complete rewrite required for .NET 6+ and Windows IoT
The nine-year hardware lifespan required two major software migrations.
4. Toolchain Obsolescence
Development tools and compilers have their own lifecycles:
GCC versions typically supported 2-3 years
Buildroot and Yocto metadata require regular updates
Debugging tools lose compatibility with newer host systems
We've encountered situations where we needed to maintain legacy build environments just to support minor updates for deployed systems.

Building Sustainable Software Ecosystems
The Long-Term Support Matrix
We've developed a tiered approach to software longevity:
Tier 1: Full LTS (10+ years)
Custom Linux distribution with backported security fixes
Regular dependency updates
Application compatibility maintenance
Reserved for critical infrastructure
Tier 2: Managed LTS (7-10 years)
Commercial Linux distribution with extended support
Limited dependency updates
Security patch backporting
Industrial and medical applications

Tier 3: Standard Support (5-7 years)
Standard enterprise Linux LTS
Security updates only
Commercial and general industrial use
Proactive Dependency Management
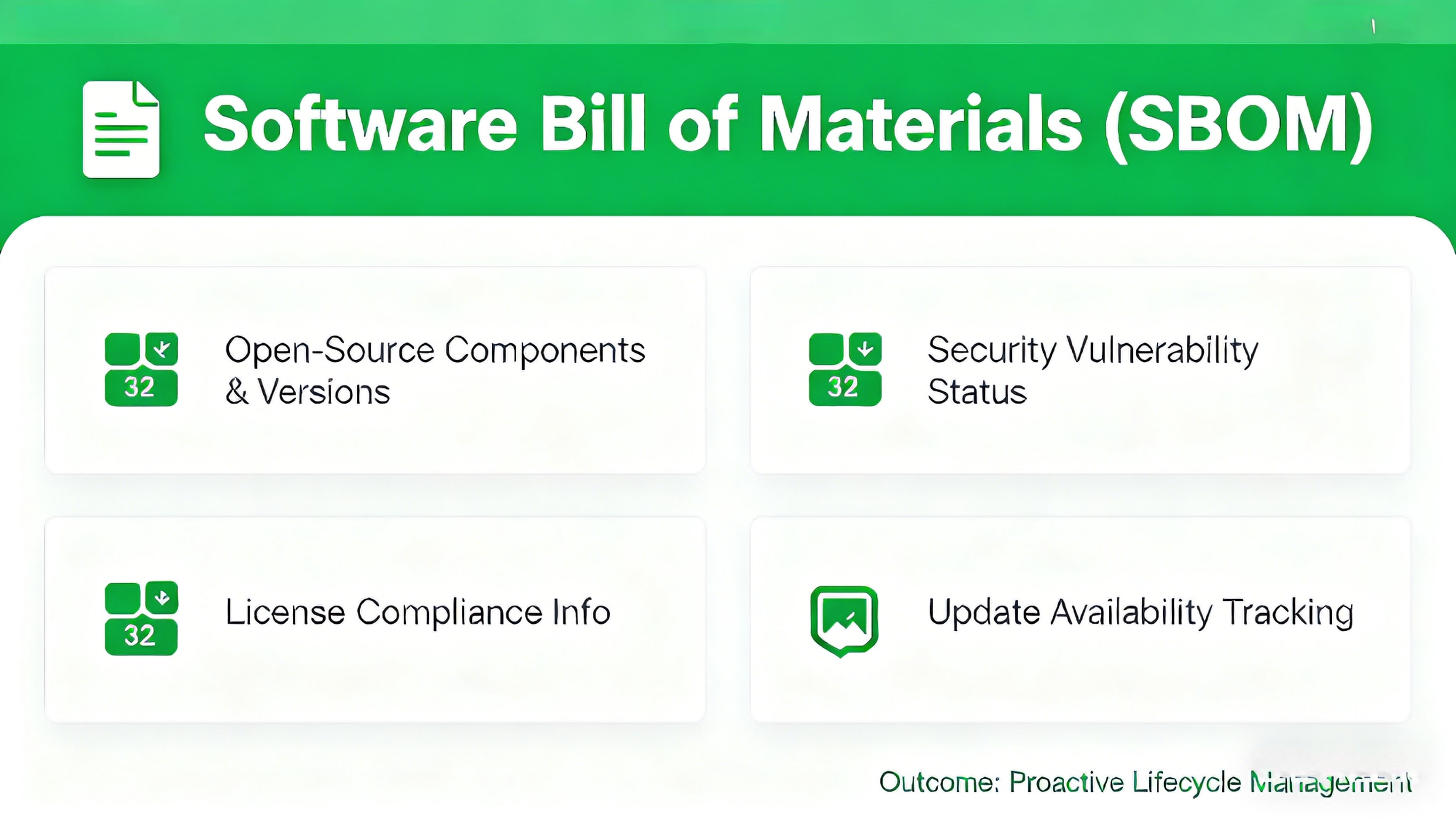
The Software Bill of Materials (SBOM) Revolution
Every embedded system we ship now includes a comprehensive SBOM detailing:
Every open-source component and version
Security vulnerability status
License compliance information
Update availability status
This enables proactive monitoring of component lifecycles and vulnerability management.
Dependency Update Strategies
Continuous: Regular updates during active development
Phased: Major updates every 2-3 years during hardware refresh
LTS-focused: Security backports only, major updates with hardware generations
Containerization: The Emerging Solution
Our industrial Linux platform now embraces containerization for long-lived deployments:
Legacy Approach:
Monolithic OS image
Tight coupling between application and OS
Difficult to update individual components
Container-Based Architecture:
Minimal base OS (10+ year support)
Application and dependencies containerized
Independent update cycles
Simplified maintenance and testing
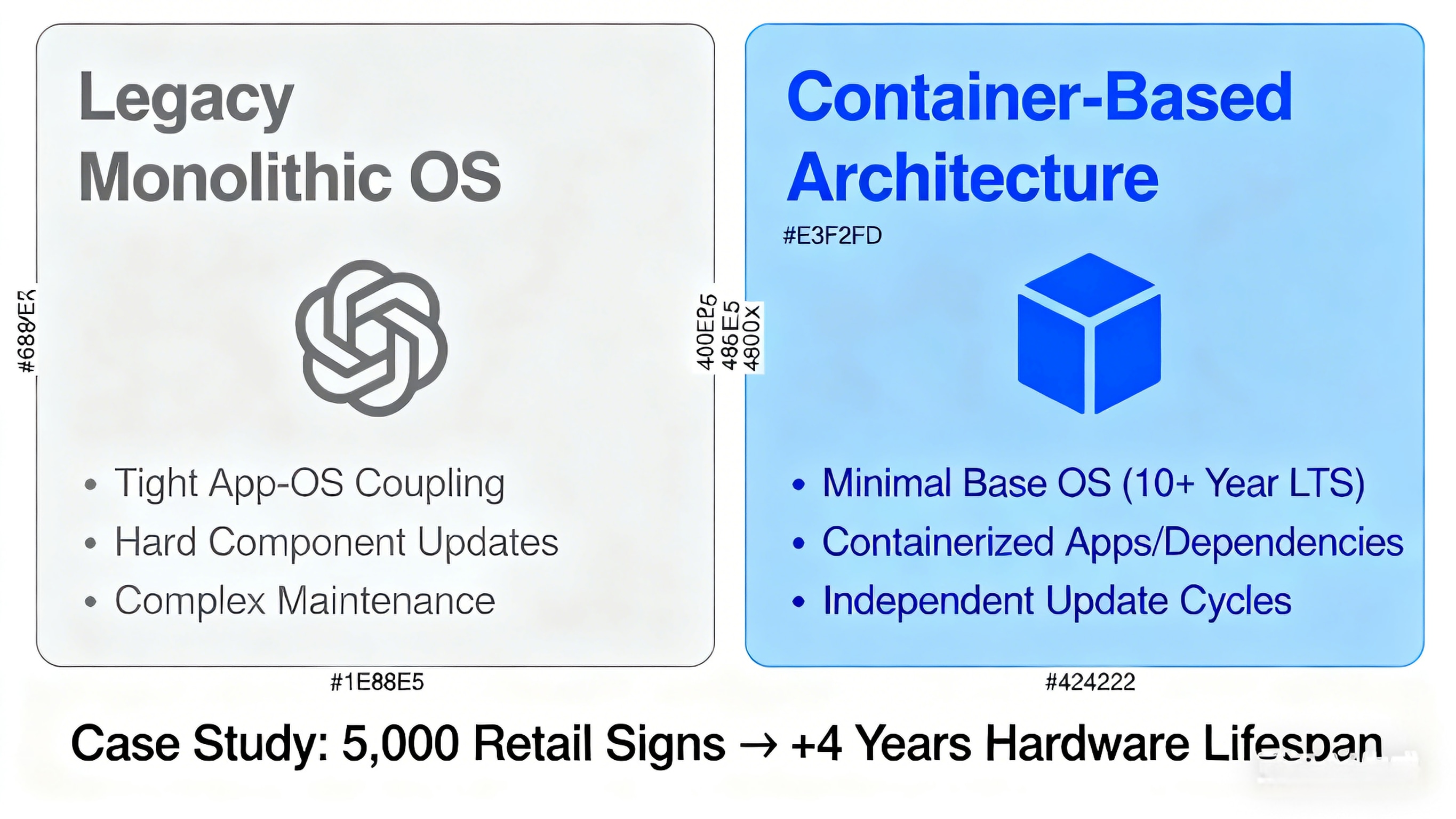
Case Study: Retail Digital Signage
A deployment of 5,000 signs migrated from monolithic images to containerized applications:
Base OS: Ubuntu 18.04 LTS (supported until 2028)
Application: Updated quarterly via containers
Result: Extended hardware lifespan by 4+ years
The Vendor Responsibility
As an ODM/OEM manufacturer, we've recognized that software longevity requires proactive measures:
Our Software Longevity Framework
Transparent Lifecycle Planning
Public software support timelines
Clear migration paths
Early EOL notifications
Update Infrastructure
Secure OTA update capabilities
Rollback mechanisms
Update verification tools
Documentation Preservation
Build environment documentation
Toolchain preservation
Knowledge transfer protocols
Contact: Tom
Phone: 86 18933248858
E-mail: tom@angxunmb.com
Whatsapp:86 18933248858
Add: Floor 301 401 501, Building 3, Huaguan Industrial Park,No.63, Zhangqi Road, Guixiang Community, Guanlan Street,Longhua District,Shenzhen,Guangdong,China
We chat
