Why Hardware-Based Security Is Your Most Overlooked Defense Layer**
Zero Trust has become the gold standard for modern cybersecurity.
Every CIO and CISO is familiar with its core principle: “Never trust, always verify.”
Yet, in the rush to deploy identity controls, network segmentation, MFA, and SASE solutions, many organizations overlook one critical truth:
Zero Trust cannot succeed if the hardware cannot be trusted.
Software-based controls can be bypassed.
Networks can be segmented.
Policies can be enforced.
But if the foundational hardware layer is compromised—BIOS, firmware, boot process, cryptographic keys—the entire Zero Trust architecture collapses from the bottom up.
This is where the concept of the Hardware Root of Trust (HRoT) becomes indispensable.
Why Hardware Root of Trust Matters More Than Ever
1. Firmware-level attacks are growing faster than OS-level exploits
Industry research shows that over 70% of advanced persistent threats (APTs) now target firmware and boot processes.
Why?
Because this layer is rarely monitored and even more rarely patched.
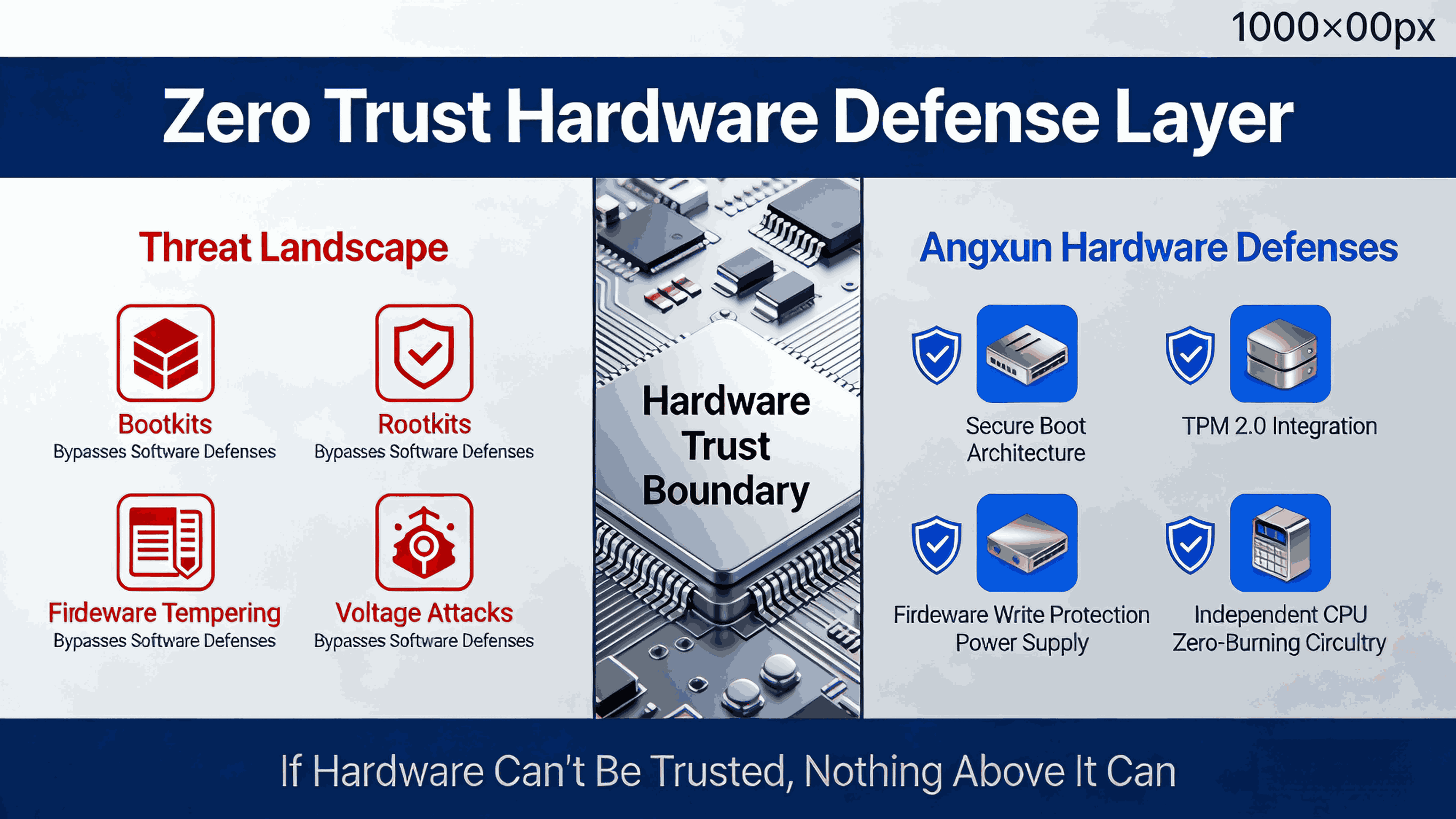
Once compromised, attackers can:
A strong Hardware Root of Trust is the only true protection against these vectors.
2. Secure Boot ensures only trusted firmware and OS components run
Secure Boot validates:
This closes the door on bootkits, rootkits, and tampered firmware—exactly the threats that bypass traditional controls.
3. TPM & cryptographic hardware are essential for Zero Trust identity
Zero Trust relies heavily on:
Device identity
Key storage
Credential protection
Remote attestation
A TPM (Trusted Platform Module) provides:
Without TPM-backed identity, Zero Trust becomes an incomplete implementation.
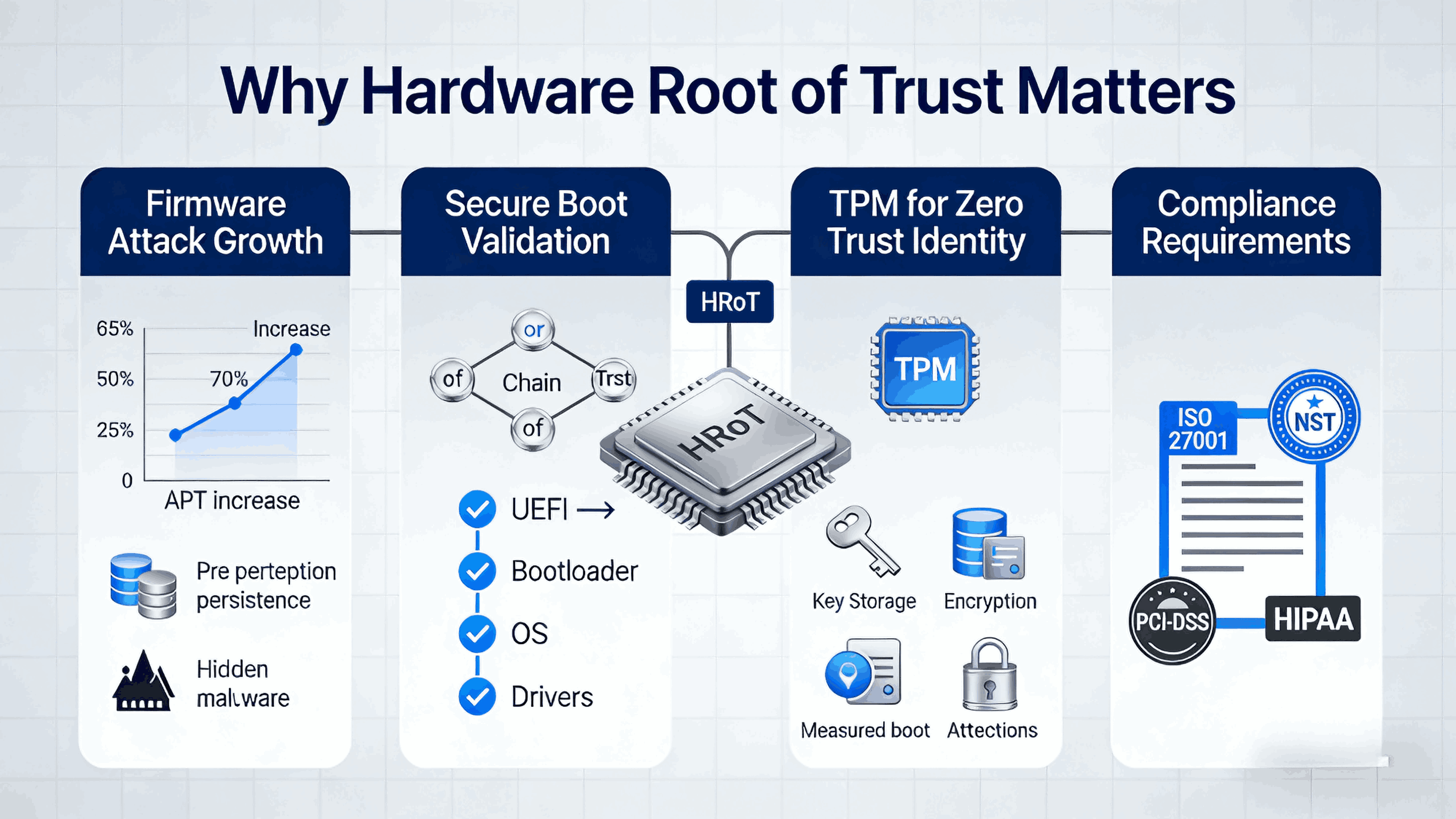
4. High-compliance industries require hardware-level assurance
Sectors such as:
must comply with strict standards (ISO 27001, NIST, PCI-DSS, HIPAA, GDPR etc.), many of which increasingly incorporate firmware integrity and hardware attestation requirements.
The Hardware Trust Layer Is No Longer Optional
Modern threats and regulations are pushing organizations to adopt:
Firmware write protection
Whitelisted BIOS configurations
Secure Boot enforcement
TPM 2.0 as baseline hardware
Continuous firmware update cycle
OS-hardware attestation models
Ignoring these requirements leaves a critical gap in your Zero Trust implementation.
How Shenzhen Angxun Technology Helps Enterprises Build a Trusted Hardware Foundation
With 24 years of OEM/ODM experience, Angxun designs hardware platforms that integrate strong hardware-based security as standard—not as an afterthought.
Company Strength
Established in 2003
10,000 m² factory, 500+ staff
Five advanced SMT production lines
High-precision SPI, AOI, ICT testing systems
300,000+ motherboard monthly capacity
CE / RoHS / FCC / ISO certifications
50+ R&D designers for BIOS + hardware security
Security-Focused Engineering Advantages
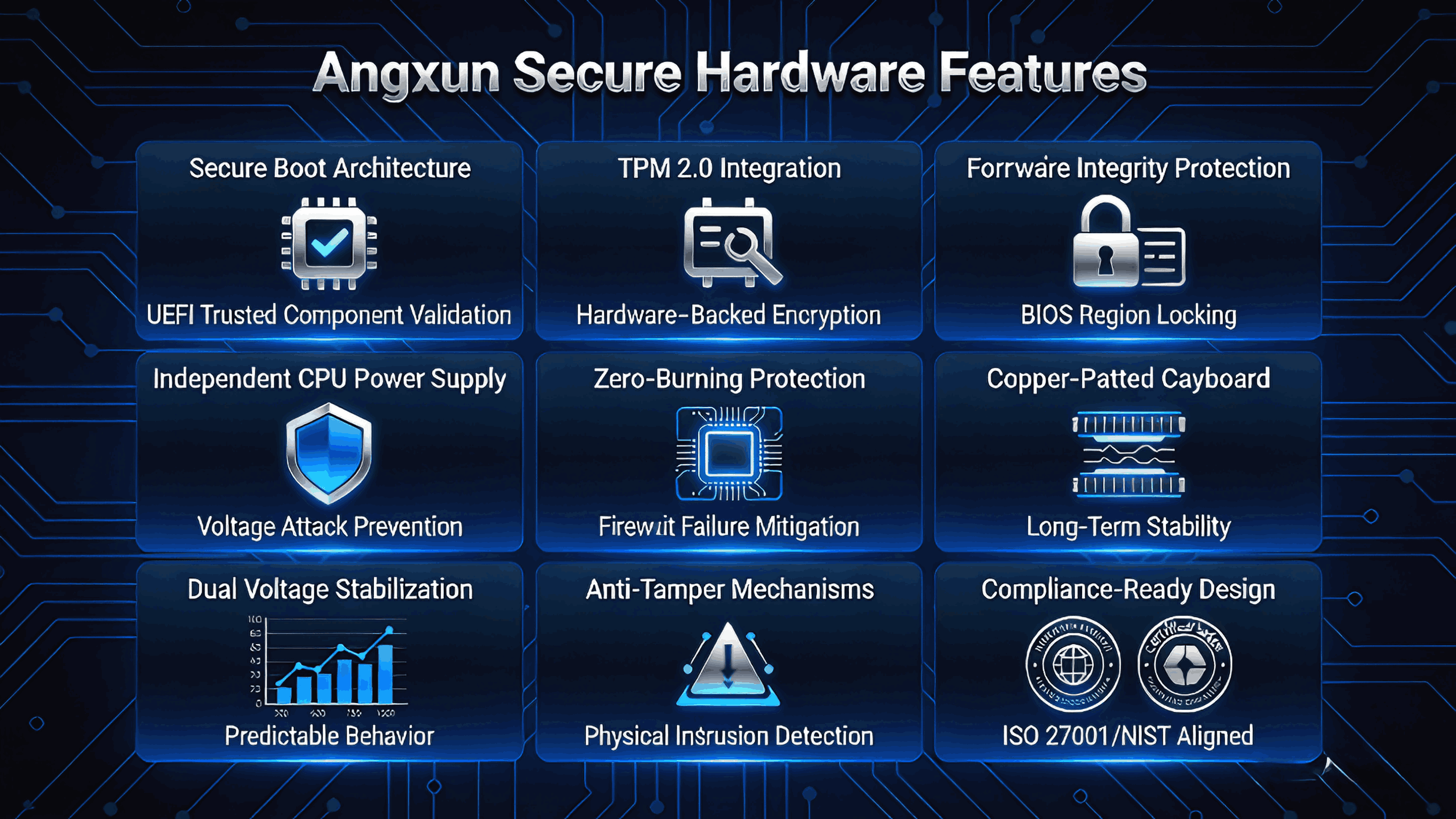
1. Secure Boot–ready architecture
Ensures only trusted firmware and OS components can execute.
2. TPM integration (TPM 2.0 optional)
Enables hardware-backed identity, encryption, and attestation.
3. Firmware integrity protection
Including write protection, BIOS-region locking, and anti-tamper mechanisms.
4. Independent CPU power supply design
Prevents malicious voltage manipulation attacks.
5. Zero-burning protection circuitry
Reduces failure rate and minimizes unauthorized power events.
6. Copper-plated PCB & all-solid capacitors
Increase long-term stability—critical for secure, multi-year deployments.
7. Dual-safety voltage & current stabilization
Ensures predictable behavior under heavy workloads.
These features form the hardware trust foundation required by modern Zero Trust strategies.
Zero Trust Starts Long Before Login — It Starts at Boot
The industry is slowly realizing:
Zero Trust is not just a network architecture.
Not just an identity framework.
Not just a software deployment pattern.
It is a hardware-first philosophy, built on immutable trust anchors that secure the system from the very first instruction executed.
If the hardware can be trusted, everything above it—OS, apps, identities, data—can be protected.
If the hardware cannot be trusted, nothing above it truly can.
Looking to strengthen the hardware layer of your Zero Trust strategy?
Shenzhen Angxun Technology offers secure, customizable Intel/AMD motherboards, industrial platforms, and embedded solutions engineered for high-compliance sectors.
Let’s build the hardware trust foundation your Zero Trust architecture needs.




